It provides standards for the appropriate administrative physical and technical safeguards to ensure the confidentiality integrity and security of protected health information. Covered entities CEs to ensure the integrity and confidentiality of information to protect against any reasonable anticipated threats or risks to the security and integrity of info and to protect against unauthorized uses or disclosure of info.
 What Is Hipaa Compliance Hipaa It Requirements Dnsstuff
What Is Hipaa Compliance Hipaa It Requirements Dnsstuff
What are the Three Standards of the HIPAA Security Rule.

The security rule protects the following. Physical Safeguards for PHI. Three main standard protections are assessed when implementing the required measures of the HIPAA Security rule. The HIPAA Security Rule establishes national standards to protect individuals electronic personal health information that is created received used or maintained by a covered entity.
Technical Safeguards for PHI. Executable files such as exe dll or scr Launching untrusted or unknown executable files can be risky as it may not be initially clear if the files are malicious. The Health Insurance Portability and Accountability Act HIPAA has a necessary provision that protects individuals electronic personal health information.
The HIPAA Security Rule is in place in order to protect patient information from the inherent security risks of the digital world. The Security Rule sets national standards for the security of electronic protected health information. Administrative safeguardsincludes items such as assigning a security officer and providing training Physical safeguardsincludes equipment specifications computer back-ups and access restriction.
There are three types of safeguards that you need to implement. Administrative physical and technical. Compliance with these standards consists of implementing administrative technical and physical safeguards to protect the confidentiality integrity and availability of electronic protected health information ePHI.
The omitted definitions by and large are technical. This is the Security Rule and it covers how these electronic data is created received processed and maintained by a covered entity. Defining rules separately from product logic has a number of advantages.
This rule blocks the following file types from launching unless they meet prevalence or age criteria or theyre in a trusted list or an exclusion list. The Security Rule requires appropriate administrative physical and technical safeguards to ensure the confidentiality integrity and security of electronic. A Covered Entity must comply with the standards and implementation specifications contained herein.
There are 3 parts of the Security Rule that covered entities must know about. The HIPAA Security Rule addresses the requirements for compliance by health service providers regarding technology security. New technology may allow for better efficiency which can lead to better care for patients but it is a double-edged sword.
The HIPAA Security Rule requires covered entities to implement security measures to protect ePHI. The Breach Notification Rule requires covered entities and business associates to provide notification following a breach of unsecured protected health information. So in actuality the Security Rule is designed to complement the Privacy Rule in its entirety.
In contrast the Security Rule covers only protected health information that is in electronic form. The HIPAA Security rules requires. The Security Rule operationalizes the protections contained in the Privacy Rule by addressing the technical and non-technical safeguards that.
The definitions below are a paraphrased subset of all the definitions contained in the HIPAA Security Rule. Understanding HIPAA Security Rule requirements will help. The HIPAA Privacy Rule protects the privacy of individually identifiable health information called protected health information PHI as explained in the Privacy Rule The Security Rule protects a subset of information covered by the Privacy Rule which is all individually identifiable health information a covered entity creates receives maintains or transmits in electronic form.
The Security Standards for the Protection of Electronic Protected Health Information the Security Rule establish a national set of security standards for protecting certain health information that is held or transferred in electronic form. Clients arent responsible for enforcing security buggy implementations will not compromise your data and most importantly youre not relying on an intermediary server to protect data from the world. Patient health information needs to be available to authorized users but not improperly accessed or used.
The HIPAA Security Rule is contained in sections 164302 through 164318. The HIPAA Security Rule requires covered entities and business associates to comply with security standards. This includes EPHI that is created received maintained.
Https Www Healthit Gov Sites Default Files Pdf Privacy Onc Privacy And Security Chapter4 V1 022112 Pdf
 What Is The Hipaa Privacy Rule
What Is The Hipaa Privacy Rule
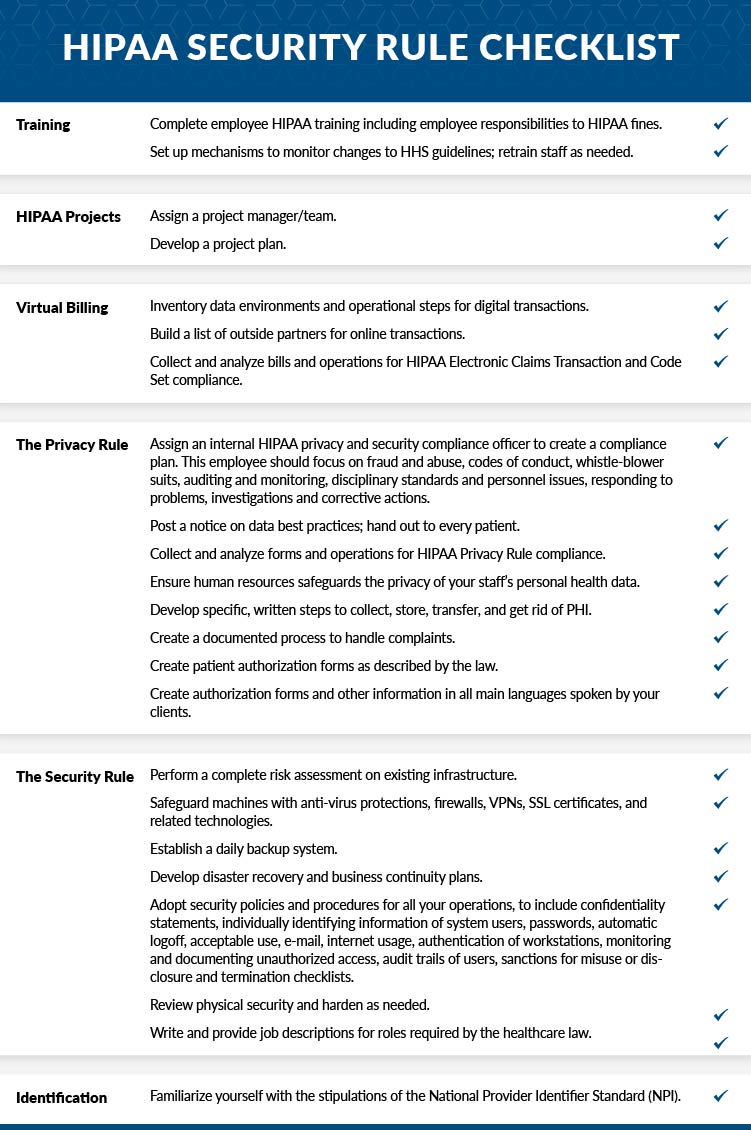 Hipaa Security Rule Checklist What Is The Hipaa Security Rule
Hipaa Security Rule Checklist What Is The Hipaa Security Rule
 What Is Hipaa Security Risk Analysis Quora
What Is Hipaa Security Risk Analysis Quora
 What Is Hipaa The Health Insurance Portability And
What Is Hipaa The Health Insurance Portability And
.jpg) Breaking Down The Hipaa Security Rule Accountable Accountable
Breaking Down The Hipaa Security Rule Accountable Accountable
 A Review Of Common Hipaa Administrative Safeguards
A Review Of Common Hipaa Administrative Safeguards
 Application Developers Guide To Hipaa Compliance
Application Developers Guide To Hipaa Compliance
 Erin Smith Aebel Board Certified Health Lawyer And Ppt Download
Erin Smith Aebel Board Certified Health Lawyer And Ppt Download
 Breaking Down The Hipaa Security Rule Accountable Accountable
Breaking Down The Hipaa Security Rule Accountable Accountable
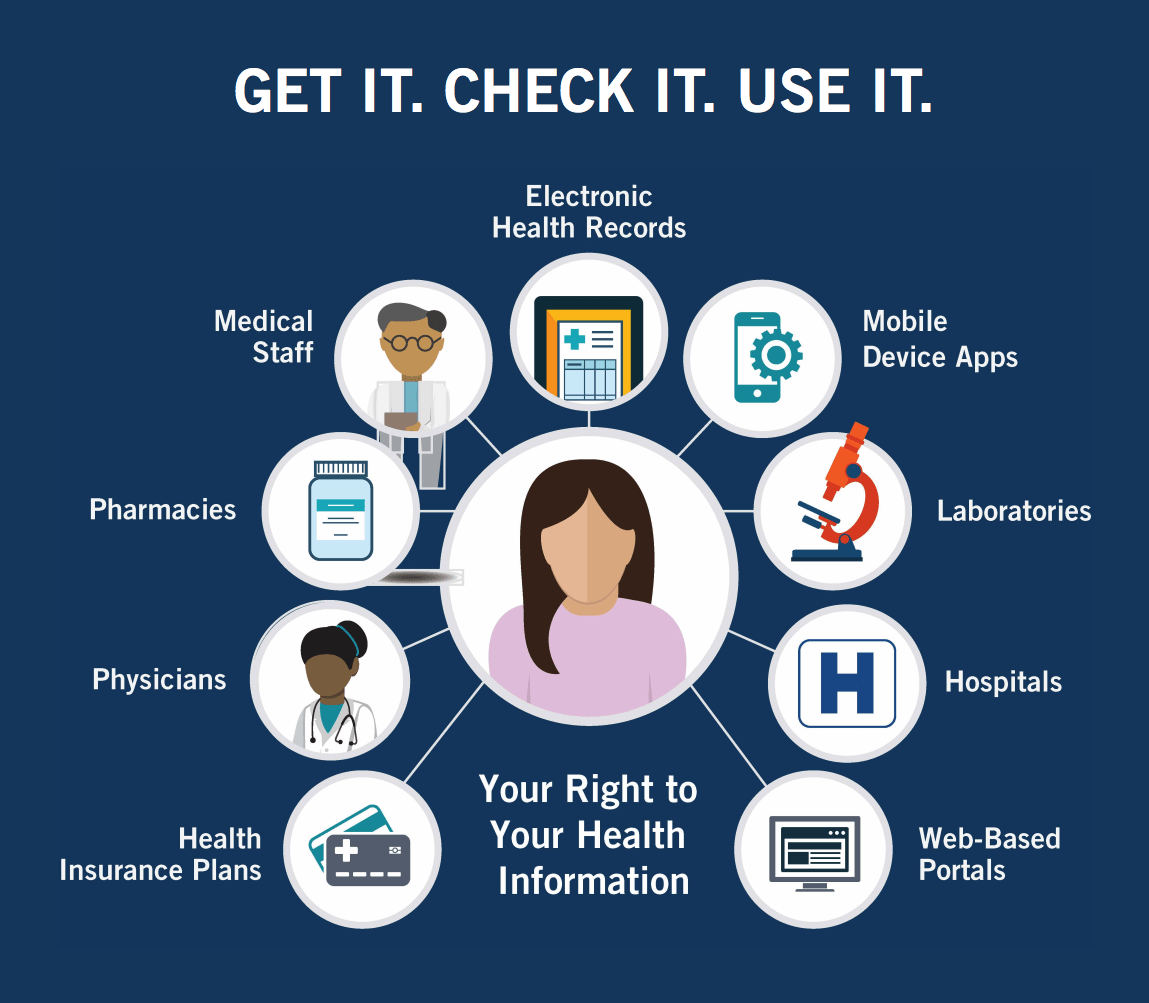 What Are The Top 5 Components Of The Hipaa Privacy Rule
What Are The Top 5 Components Of The Hipaa Privacy Rule
 What Is Hipaa Compliance Hipaa It Requirements Dnsstuff
What Is Hipaa Compliance Hipaa It Requirements Dnsstuff


No comments:
Post a Comment
Note: Only a member of this blog may post a comment.